Are you looking to enhance your IoT infrastructure with AWS IoT Core while ensuring secure access through SSH? AWS IoT Core SSH is a powerful combination that allows you to manage and secure your IoT devices effectively. Whether you're a developer, IT professional, or business owner, understanding how to integrate AWS IoT Core with SSH is crucial for maintaining robust and secure connectivity. In this article, we’ll explore everything you need to know about AWS IoT Core SSH, from its core concepts to practical implementation strategies.
With the growing importance of IoT in various industries, ensuring secure and reliable communication between devices is more critical than ever. AWS IoT Core provides a scalable and secure platform for managing IoT devices, while SSH (Secure Shell) offers encrypted communication channels. Together, they form a powerful solution for managing IoT ecosystems securely. In the following sections, we'll dive deep into the technical aspects, benefits, and best practices for leveraging AWS IoT Core SSH in your projects.
This guide is designed to provide expert insights, actionable advice, and trustworthy information to help you navigate the complexities of AWS IoT Core SSH. Whether you're new to IoT or an experienced professional, this article will equip you with the knowledge you need to succeed. Let’s explore how AWS IoT Core SSH can revolutionize your IoT infrastructure.
Read also:Exploring Eden Fantasies A Journey Into Paradise
Table of Contents
- Introduction to AWS IoT Core
- Understanding SSH (Secure Shell)
- Integration of AWS IoT Core and SSH
- Key Benefits of Using AWS IoT Core SSH
- Step-by-Step Guide to Setting Up AWS IoT Core SSH
- Best Practices for Securing AWS IoT Core SSH
- Common Challenges and Solutions
- Real-World Use Cases of AWS IoT Core SSH
- Tools and Resources for AWS IoT Core SSH
- Conclusion and Next Steps
Introduction to AWS IoT Core
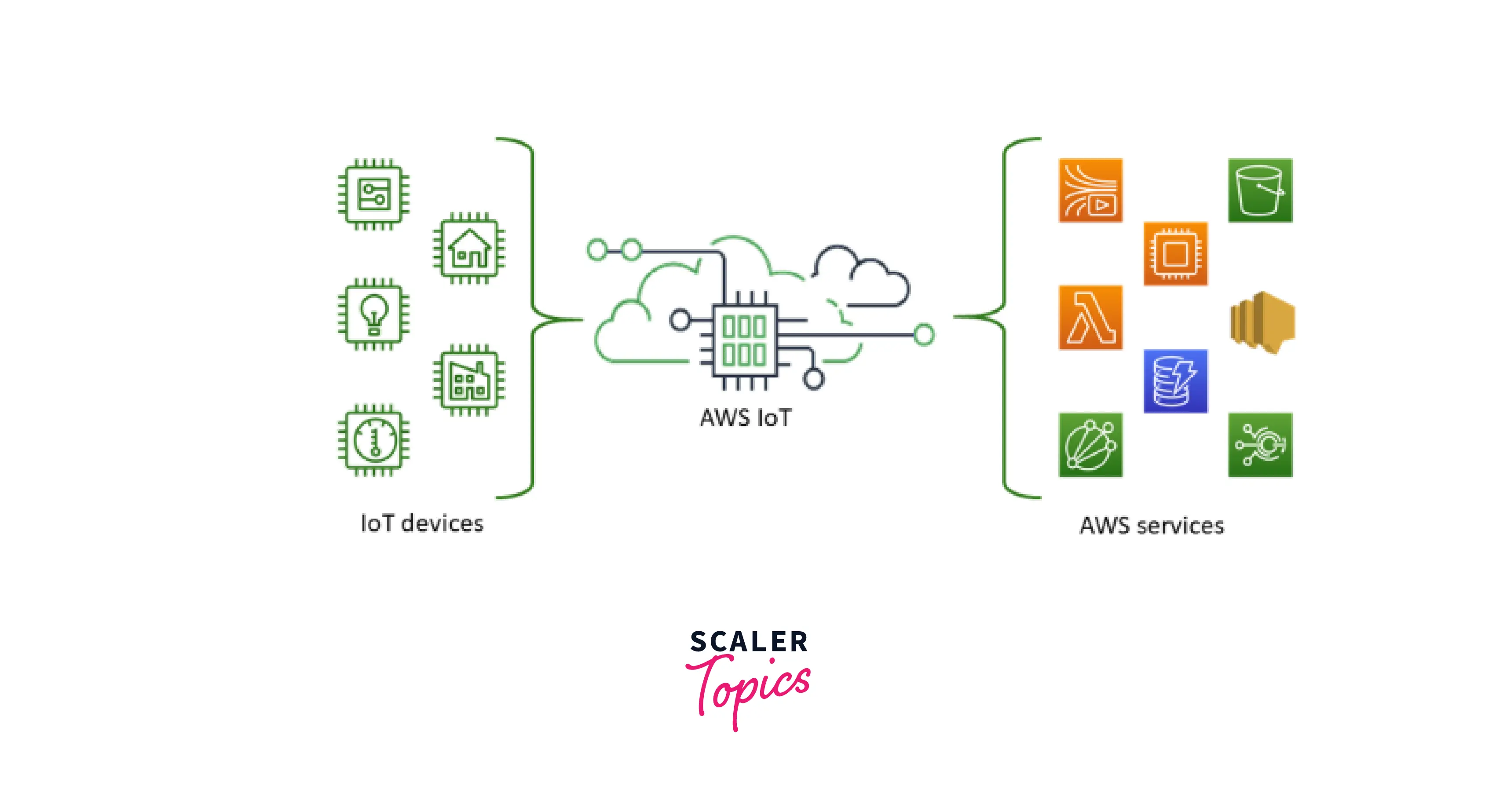
AWS IoT Core is a managed cloud service that lets connected devices easily and securely interact with cloud applications and other devices. It supports billions of devices and trillions of messages, ensuring reliable communication even in highly scalable environments. AWS IoT Core provides features like device shadowing, rules engine, and secure authentication, making it a go-to solution for IoT projects.
One of the standout features of AWS IoT Core is its ability to integrate with other AWS services, such as AWS Lambda, Amazon S3, and Amazon DynamoDB. This integration allows developers to build end-to-end IoT solutions that are both scalable and secure. Additionally, AWS IoT Core supports multiple protocols, including MQTT, HTTP, and WebSocket, ensuring compatibility with a wide range of devices.
For businesses, AWS IoT Core offers significant advantages, such as reduced operational costs, improved scalability, and enhanced security. By leveraging AWS IoT Core, organizations can focus on innovation and growth while leaving the complexities of IoT management to AWS.
Understanding SSH (Secure Shell)
SSH, or Secure Shell, is a cryptographic network protocol used for secure communication over unsecured networks. It provides strong encryption and authentication mechanisms, making it an ideal choice for managing remote devices securely. SSH is widely used in IT operations for tasks like remote server management, file transfers, and secure command execution.
The primary components of SSH include the SSH client, SSH server, and encryption algorithms. The SSH client initiates the connection, while the SSH server authenticates and authorizes the client. Encryption algorithms ensure that all data exchanged between the client and server is secure and tamper-proof.
SSH is particularly relevant in IoT environments, where devices often operate in unsecured networks. By using SSH, IoT devices can communicate securely with cloud services and other devices, reducing the risk of unauthorized access and data breaches.
Read also:Net Worth Of Bernie Sanders Wife A Comprehensive Analysis
Integration of AWS IoT Core and SSH
Integrating AWS IoT Core with SSH involves setting up secure communication channels between IoT devices and AWS services. This integration ensures that data transmitted between devices and the cloud is encrypted and authenticated, providing an additional layer of security.
Why Integrate AWS IoT Core with SSH?
- Enhanced Security: SSH encryption ensures that sensitive data is protected from eavesdropping and tampering.
- Remote Management: SSH allows administrators to manage IoT devices remotely, reducing the need for physical access.
- Scalability: AWS IoT Core’s scalability combined with SSH’s secure communication capabilities makes it ideal for large-scale IoT deployments.
How Does the Integration Work?
The integration process typically involves configuring SSH keys, setting up SSH servers on IoT devices, and using AWS IoT Core’s secure communication features. AWS IoT Core provides APIs and SDKs that simplify the integration process, allowing developers to focus on building robust IoT solutions.
Key Benefits of Using AWS IoT Core SSH
Using AWS IoT Core SSH offers numerous benefits for businesses and developers. Below are some of the key advantages:
1. Enhanced Security
AWS IoT Core SSH ensures that all communication between IoT devices and the cloud is encrypted, reducing the risk of data breaches. SSH’s strong authentication mechanisms also prevent unauthorized access to devices and data.
2. Simplified Device Management
With SSH, administrators can remotely manage IoT devices, perform updates, and troubleshoot issues without needing physical access. This capability is particularly useful for large-scale IoT deployments.
3. Scalability and Flexibility
AWS IoT Core’s scalability combined with SSH’s secure communication capabilities makes it easy to manage thousands or even millions of IoT devices. The flexibility of SSH also allows it to be used in various IoT use cases, from smart homes to industrial automation.
Step-by-Step Guide to Setting Up AWS IoT Core SSH
Setting up AWS IoT Core SSH involves several steps, from configuring SSH keys to integrating with AWS IoT Core. Below is a detailed guide to help you get started:
Step 1: Generate SSH Keys
SSH keys are used to authenticate devices and users securely. To generate SSH keys, use the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"This command generates a public and private key pair. Store the private key securely and add the public key to your IoT devices.
Step 2: Configure SSH on IoT Devices
Install and configure an SSH server on your IoT devices. For example, on Linux-based devices, you can install OpenSSH using the following command:
sudo apt-get install openssh-serverOnce installed, configure the SSH server by editing the /etc/ssh/sshd_config file to enable key-based authentication and disable password-based login for added security.
Step 3: Integrate with AWS IoT Core
Use AWS IoT Core’s APIs and SDKs to integrate SSH with your IoT devices. Configure device policies and rules in AWS IoT Core to ensure secure communication between devices and the cloud.
Best Practices for Securing AWS IoT Core SSH
To maximize the security of your AWS IoT Core SSH setup, follow these best practices:
- Use strong, unique SSH keys for each device.
- Regularly update SSH server software to patch vulnerabilities.
- Implement multi-factor authentication (MFA) for additional security.
- Monitor SSH logs for suspicious activity and unauthorized access attempts.
Common Challenges and Solutions
While AWS IoT Core SSH offers numerous benefits, it also comes with its own set of challenges. Below are some common issues and their solutions:
Challenge 1: Managing SSH Keys
Managing SSH keys for thousands of devices can be challenging. To address this, use a centralized key management system like AWS Key Management Service (KMS).
Challenge 2: Ensuring Compatibility
Not all IoT devices support SSH out of the box. To overcome this, use lightweight SSH implementations like Dropbear or customize the SSH configuration to meet device requirements.
Real-World Use Cases of AWS IoT Core SSH
AWS IoT Core SSH is used in various industries to enhance IoT security and efficiency. Below are some real-world examples:
1. Smart Home Automation
Home automation systems use AWS IoT Core SSH to securely manage smart devices like thermostats, lights, and security cameras.
2. Industrial IoT
In industrial settings, AWS IoT Core SSH is used to remotely monitor and manage machinery, ensuring secure and reliable operations.
Tools and Resources for AWS IoT Core SSH
To help you get started with AWS IoT Core SSH, here are some useful tools and resources:
Conclusion and Next Steps
AWS IoT Core SSH is a powerful combination that enhances the security and efficiency of IoT ecosystems. By integrating AWS IoT Core with SSH, businesses can ensure secure communication, simplify device management, and scale their IoT deployments effectively.
To take your IoT projects to the next level, consider implementing AWS IoT Core SSH in your infrastructure. Start by generating SSH keys, configuring SSH on your devices, and integrating with AWS IoT Core. Follow best practices to maximize security and efficiency.
We’d love to hear your thoughts! Share your experiences with AWS IoT Core SSH in the comments below or explore more articles on our website for additional insights.